
You arrive to work Monday morning after a long weekend to find this email in your inbox.

Only one (big) problem: you didn’t sign in to your account over the weekend. You’ve been breached!
While it’s not possible to 100% prevent email security compromises, it is possible to drastically reduce their likelihood.
There are three universal cybersecurity controls that should be in place at all businesses. Two of them are tech tools that can and should be used on personal accounts too.
- Cybersecurity Training
- Password Manager
- Multi-Factor Authentication
We’ve covered password managers a couple of times before. Today, we’ll take a quick dive into multi-factor authentication.
What is Multi-Factor Authentication?
Multi-factor authentication, frequently referred to as MFA, is a security control that requires users to provide a second form of authentication when logging into a device.
The first authentication method is typically a traditional password. The user enters it first (hopefully with a password manager!) and is then prompted to enter a one-time password as the second authentication factor.
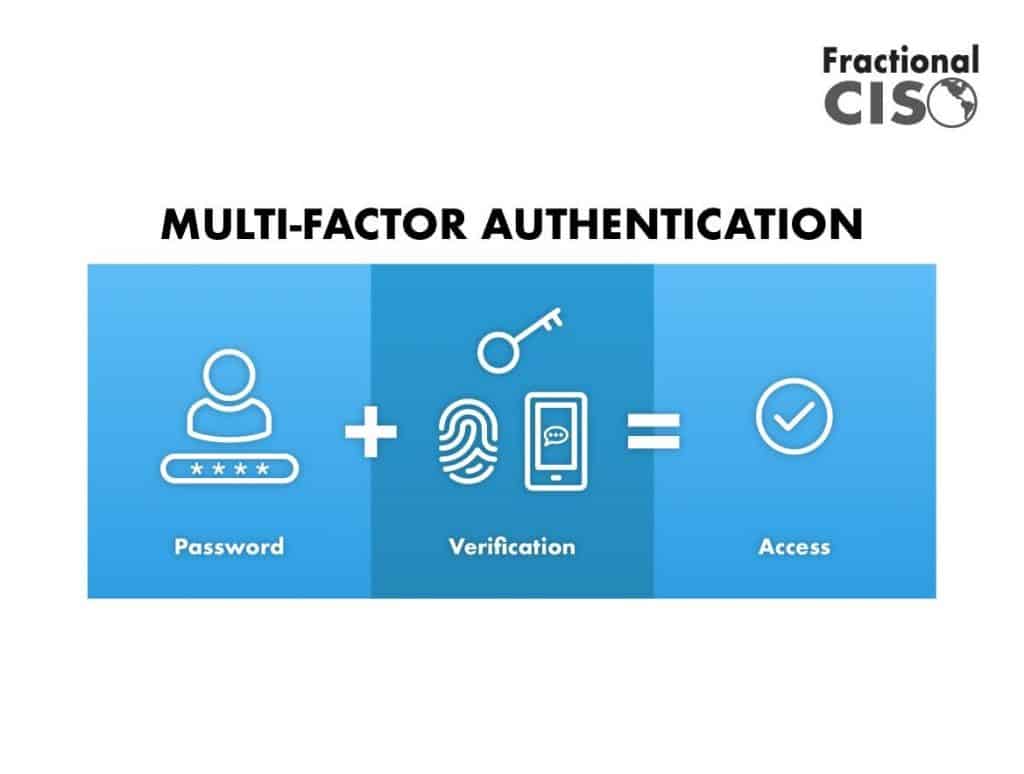
This password can be delivered in a number of ways. The most common way is a text (SMS) message. It can also be sent via an email or through an authenticator app.
This additional layer of authentication helps to stop an attacker from accessing the account even if the first password is compromised. Access is only granted when both passwords are entered, and the second password is generated and sent to the device of the account holder.
This usually, depending on the method, has the added benefit of immediately notifying the user of an unauthorized sign-in attempt, allowing them to take action to resecure their account.
Microsoft tracks hundreds of millions of malicious login attempts daily and has scored MFA as 99.9% effective.
MFA is not infallible. It can be compromised, and some methods are less secure than others.
SMS, the most widely used form of MFA, is actually the least secure method of MFA available thanks to security issues inherent in the telephone network.
Text (SMS) Multi-Factor Authentication vs Other Methods
SMS is the most popular MFA method since it’s easy to enable and start using. It’s widely supported by a large number of companies (though not all, Disney+ is a notable exception) and convenient to use. Modern smartphones can recognize an MFA text and allow you to copy your one time password for easy use.
The problem with SMS is that it’s transmitted in cleartext and can be easily intercepted by determined attackers. SMS-based one-time codes are also phishable via open source and readily available phishing tools.
Further, phone network employees can be tricked into transferring phone numbers to a threat actor’s SIM card, allowing attackers to receive MFA one-time codes on behalf of their victims.
Want proof that this can happen? Reddit had a serious security incident in 2018 where the primary vector of attack was SMS intercept.
“On June 19, we learned that between June 14 and June 18, an attacker compromised a few of our employees’ accounts with our cloud and source code hosting providers. Already having our primary access points for code and infrastructure behind strong authentication requiring two factor authentication (2FA), we learned that SMS-based authentication is not nearly as secure as we would hope, and the main attack was via SMS intercept. We point this out to encourage everyone here to move to token-based 2FA.”
– Chris Slowe, Reddit CTO
This is not to say that SMS MFA is awful and you should never use it. If SMS is the only form of MFA available for an account, you should definitely be using it. A worse version of MFA is significantly better than no MFA!
You should learn from others’ mistakes though, and use a more secure form of MFA if one is available to you.
Alternatives to Text (SMS) Multi-Factor Authentication
Authenticator Apps
Phone-based authenticator apps generate time-based codes that rotate constantly through the app. The codes generated in the app are tied to the device itself rather than your online identity. When you login to an account, you open up the application to access the code.
Authenticator apps themselves are not password protected, but cell phones should be locked down with a password and biometrics. In order to gain access to your account, an attacker would need to get the password to the account, take possession of your cell phone, crack the cell phone, and open the authenticator app. This is a much bigger task than just cracking a password and intercepting SMS!
There are a plethora of authenticator apps available. Some popular ones include Google Authenticator, Authy, LastPass Authenticator, and Microsoft Authenticator. They all have different features that may serve your needs better than others. For example, Authy has a backup feature for if you lose your phone and LastPass Authenticator integrates with the LastPass password manager.
Security Keys
Security keys are a form of passwordless authentication. Users plug the hardware “keys” into computers like USBs and then tap them with their finger to authenticate the application they are trying to access. Hardware keys are only ideal when the user configures their account so that other account recovery options are not available at login.
Should you use SMS or App-Based Multi-Factor Authentication?
Multi-factor authentication is a universal cybersecurity control that anyone can benefit from. It’s also one of the easiest to implement, both on personal and business accounts.
Whatever you do, utilize some form of MFA. Some are better than others, but all are better than nothing!
Want to get great cybersecurity content delivered to your inbox? Sign up for our monthly newsletter, Tales from the Click! https://fractionalciso.com/newsletter/
Chinmayee Paunikar also contributed to this article.